![[Steve Friedl Logo]](/images/unixwiz-logo-140x80.gif)
This site uses advanced css techniques
On around 23 Sept, 2009, Paychoice's "Online Employer" portal had a security incident where portal users received emails purportedly from Paychoice, informing them that they had to download and install an update to work with the portal.
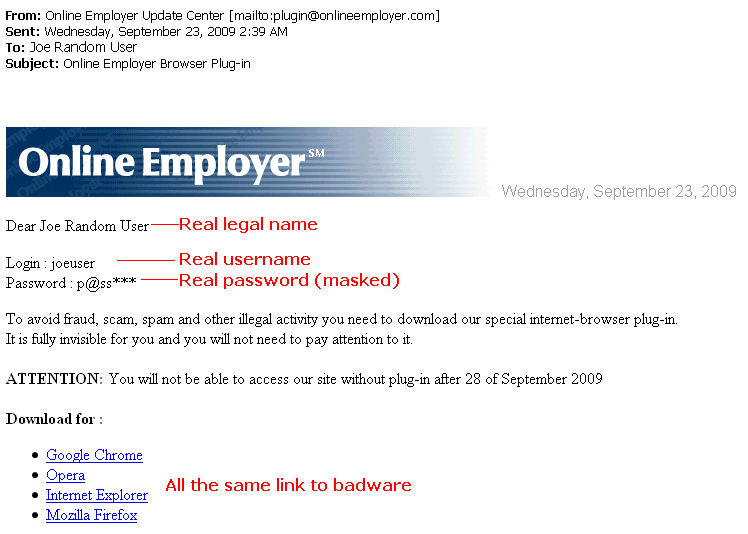
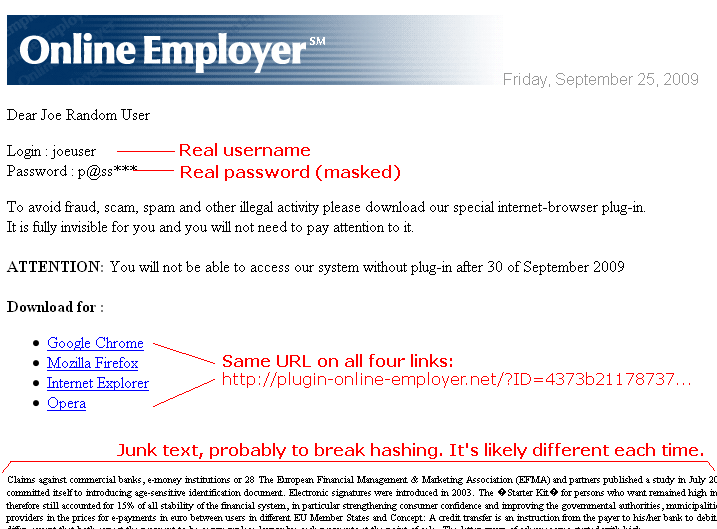
The English was not particularly well written, but the email included their portal username and part of their real password. This was not a random phishing expedition: somebody had private information.
The links were to websites hosted at Yahoo!, and the badware was a password-stealing Trojan horse that phones home its stolen information to a webserver in Sweden.
It's said that Paychoice took down the portal at ~noon on Wednesday and provided new usernames and passwords. Apparently, a lot of service bureaus had some very uncomfortable phone calls to make, while many of their staff were at the Paychoice annual user conference.
I became involved on Thursday afternoon when a customer casually mentioned that he was having a bad day, and that started the process: I'm a security consultant.
The log below represents activies that I was directly involved in; there have been rumors and claims of other events or actions; I'll not address them.
Update 2009/09/30 — After following this incident for almost a week, I've come to the conclusion that this is far less serious than it appears at first. The bad guy did not get private data, and it was not an inside job. I have written my analysis here, though of course this is all speculation.
(All times are Pacific Daylight Time)
update - onlineemployer . com online - employer - dnl . com
onlineemployer - update . net onlineemployer - download . net secure - onlineemployer . com plugin - online - employer . org
onlineemployer - download . biz plugin - online - employer . com plugin - online - employer . net
PAYCHOICE SOFTWARE Support Notification September 24, 2009 PayChoice continues to investigate a security incident with Online Employer that began Wednesday morning. Access to Online Employer was reactivated shortly after 12:00 am yesterday. We have provided new credentials to the licensee service bureau users and, working with the licensees, are in the process of providing the same information to company and employee users. For the third day, some registered users received emails from a sender not affiliated with PayChoice directing them to a website to download and install a plug-in that would be required to view the site. PayChoice again notified users that the plug-in was not required and directed them not to download or install it. After reviewing the content of the emails, we have concluded that valid user IDs were included in the message. Additionally, some emails included 4 characters of a valid password. At this time, we have no evidence that any other confidential data has been accessed. We have engaged Symantec, a leading provider of computer security and anti-virus solutions, in the analysis of the plug-in being provided by the email sender. While the assessment is continuing, the initial feedback is that the purpose of the plug-in is to block browser access to certain websites that have names similar to that of online-employer.com. Our security expert consultants are working on a number of different fronts. First, they are working to neutralize the sender web sites from which the plug-ins are downloaded. This would preclude the infection of any user machines that receive the email and follow the links. Second, they are working to neutralize the sites from which the emails are generated so no further emails are sent from those sites. Thirdly, they are beginning to perform forensics on the PayChoice infrastructure to determine how the information used in the emails was acquired by the sender. Fourthly, they are attempting to determine if any other confidential data has been accessed. Finally, the law enforcement agencies are escalating this matter to the appropriate authorities. PayChoice is committed to the secure handling of all client data and will send further communications as events dictate to keep you informed.
onlineemployer - download . biz plugin - online - employer . com plugin - online-emp . info onlimemp - plugin . com onlimemp - software . org
Date: Fri, 25 Sep 2009 11:47:20 -0700
From: Steve Friedl <steve@unixwiz.net>
To: support @ paychoice.com
Cc: {Yahoo! Security email}
Subject: Paychoice / Yahoo! Security
Good morning,
I'm a security consultant working with a number of Paychoice licensees
on the excitement of late, and have also been working with Yahoo! to
have the malware domains taken down as we find them. It's been maybe a
dozen or so by now.
Yahoo! Security would like to get in touch with somebody at Paychoice
regarding this, to perhaps put your heads together.
Could somebody from Paychoice please contact {Yahoo! Security email}
They know who you are and will be expecting your email.
Good luck with this - I know it's been really awful for you folks.
Steve
From: Thomas McNeila Sent: Friday, September 25, 2009 1:41 PM To: (customers) Subject: Online Employer Security Update Over the past three days, you may have received emails from a sender not affiliated with PayChoice with the subject line "Online Employer Browser Plug-in", or something similar, requesting you to download a plug-in to access your online account information. Immediately delete these messages. DO NOT OPEN THEM or click on any of the links in the email. This plug-in is not required to view Online Employer or any of the PayChoice websites. It is possible that you will receive similar emails in the future, and you should continue to immediately delete them. Because of this third party email activity, new login ID's have been issued and user passwords have been expired. Users will be able to access the site with their new login ID and their current password, and will then be required to select a new password prior to being able to access any other website functionality. These changes will ensure that your data is protected. At this time, we have no evidence that any other confidential data has been accessed. We apologize for this inconvenience. We have engaged Symantec, a leading provider of computer security and anti-virus solutions, and SecureWorks, a world-class information security services provider, in the analysis of the plug-in being provided by the email sender. The assessment is continuing, and PayChoice will provide additional details as they become available. Users who have selected the link and have the plug-in installed on their computers should shut them down and refrain from using them until the purpose of the plug in and a mechanism for removal can be determined. If you do not have an alternate computer from which to access Online Employer, please call your Support Representative for assistance. Our security expert consultants are working on a number of different fronts. * Working to neutralize the sender web sites from which the plug-in is downloaded. This would preclude the infection of any user machines that receive the email and follow the links. * Working to neutralize the sites from which the emails are generated so no further emails are sent from those sites. * Beginning to perform forensics on the PayChoice infrastructure to determine how the information used in the emails was acquired by the sender. * Attempting to determine whether any other confidential data has been accessed. The law enforcement agencies are escalating this matter to the appropriate authorities. PayChoice is committed to the secure handling of all client data and will send further communications as events dictate to keep you informed. If you require assistance with your login access please contact your Support Representative. Should you require assistance after hours or over the weekend please contact us via the Support Call Center and include your contact information so we may reach you. Thank you for your understanding and patience. The following information may be useful to distribute to your client base to assist in implementing secure procedures. ********************************************************** Things to look for to avoid scam email and Web sites: Fraudulent email and Web sites are designed to deceive you and can be difficult to distinguish from the real thing. * Whenever you get an email about your Online Employer account, the safest and easiest course of action is to open a new web browser, type https://www.onlineemployer.com, and log in to your Online Employer account directly. Do not click on ANY link in an email that requests personal information. To help you better identify fake or fraudulent emails, we follow strict rules. We will never ask for the following personal information in an email: * Credit and debit card numbers * Bank account numbers * Social Security Numbers * Employer tax ID numbers * Driver's license numbers * Email addresses * Passwords An authentic Online Employer email will never include: * Attachments (other than a pdf) * Software * A link to download anything that is not from our website directly How to report a suspicious email or other activity regarding your Online Employer account: * Contact your payroll provider immediately with as much detail as possible. * Do not alter the subject line or forward the message as an attachment. * Delete the suspicious email from your account. * Follow your internal security procedures More steps to help protect you from vulnerability: * Monitor your account. Check your account periodically for suspicious activity. If you notice unauthorized use, report it to us. * Keep your security software current. Update your firewalls and security patches frequently. * Be smart about your password. Change passwords often and use unique passwords that include letters, numbers, symbols as well as upper and lower case text. If you require assistance with your login access please contact your Support Representative.
This page will be updated as events unfold.
Though I've performed security responses like this for years, in this case I have a substantial conflict of interest: I do consulting in the payroll industry, and am closely associated with a competitor of Paychoice.
My efforts on this security response were strictly a private effort to protect customers, have been entirely off the clock (of anybody), and have not been coordinated with any other party.
I have no axe to grind with Paychoice — with whom I have a great deal of sympathy — and believe I'm presenting this information in good faith. But you can reach your own conclusions based on what you read here and elsewhere.