![[Steve Friedl Logo]](/images/unixwiz-logo-140x80.gif)
This site uses advanced css techniques
Windows 7 is now in Release Candidate status (build 7100, May 2009), and many are trying this new operating system. Those who skipped past Vista from XP are finding a new experience and an entirely new security paradigm: User Account Control.
UAC was introduced with Vista and was widely maligned due to its in-your-faceness, and though it's calmed down some as Vista has been updated, it seems to have really hit its stride in Windows 7. I like UAC a lot.
But even in its imperfect form, it was a good idea, attempting to brighten the terribly blurry line between administrative tasks and user tasks that has plagued Windows since the early days.
Much of this is due to the early consumer operating systems Win95, Win98, and WinME, which maintained no technical distinction between these roles: everybody was always an administrator, and software developers had no way of even thinking about a separation of roles.
But even with the more modern NT-based systems Windows 2000 and Windows XP, it was so painful to really get your work done as a non-administrative user that most people simply gave up and ran with an admin account. This was almost entirely due to poor habits by software developers: they themselves ran as admins, and simply wrote sloppy code that assumed everybody was one too.
Microsoft has been trying very hard to counter this everybody-is-an-admin mentality, and UAC was their attempt at compromise: if you're going to run as admin, at least we can make you aware of the role differences. This is what UAC is attempting to do.
User Account Control works by guarding access to administrative rights, and this involves elevations of privilege: when attempting to perform admin tasks, the operating system either auto-elevates to admin rights, or requests some kind of consent or credentials to do so.
Windows 7 recognizes three broad classes of users:
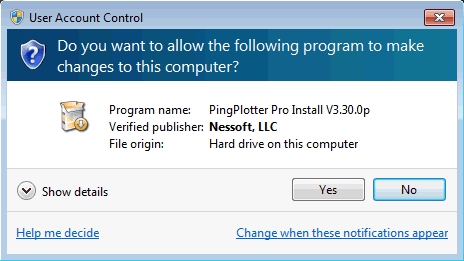
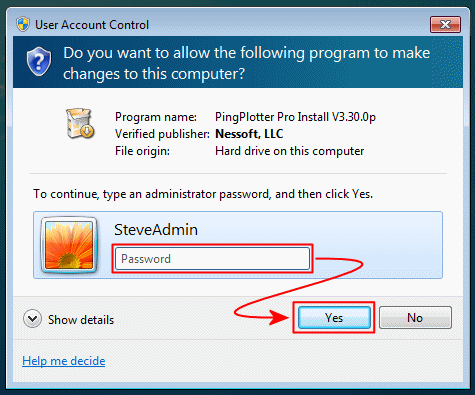
I strongly believe in limited user accounts!
I've been doing so since XP Service Pack 2, including my laptop and main software-development workstation. It's been painful at times, but it's dramatically lowered the attack surface of my system and has contributed to my Windows machines never suffering a compromise.
Stepping into Windows 7, I of course wanted to run as a limited user, but because I didn't know how it worked (in Win7 or in Vista), I essentially locked myself out of my own machine (see below).
So after figuring it out (and reinstalling a couple of times), I created this Tech Tip to assist a security-minded user to do the safe thing.
This paper presents two procedures: one for a first-time install of the operating system, and one for retrofitting an already-installed system where the main user is a custom admin.
A new install is the easiest to get right because there's no prior setup to work around, and the illustration uses two Windows accounts:
The built-in Administrator will not be used in any way, and will remain disabled.
Take these steps to set up Windows 7:
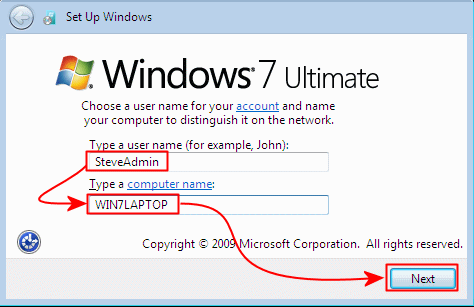 Install Windows 7, creating a initial user "SteveAdmin"
Install Windows 7, creating a initial user "SteveAdmin"
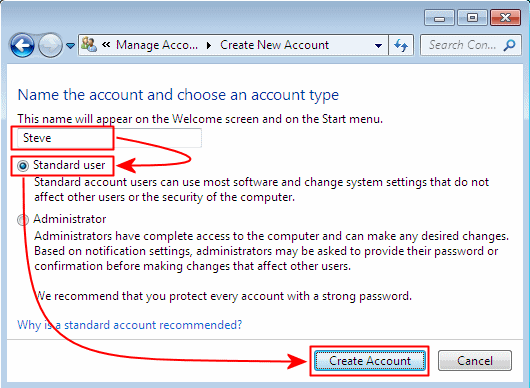 Create a new account "Steve" as a standard user
Create a new account "Steve" as a standard user
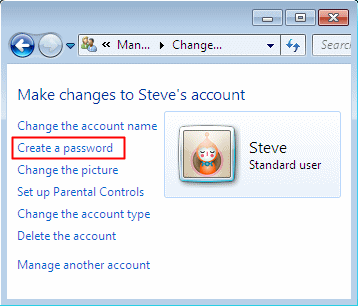 Assign a password to the new user "Steve" (if desired)
Assign a password to the new user "Steve" (if desired)
If you do this, Steve will lose all EFS-encrypted files, personal certificates and stored password for Web sites or network resources.
Now that we're a standard user, attempts to perform admin tasks are greeted with a UAC prompt for SteveAdmin's password.
This method is used if Windows 7 has been already set up, where the installer user (here: Steve) was automatically created with administrative rights. Though one could technically rename the account to SteveAdmin and make a new Steve as a limited user, this would play havoc with the user profiles, the desktop, and other personal configurations. It's possible to copy profiles around, but it's easier to just create a new admin account and demote this one.
These are the steps:
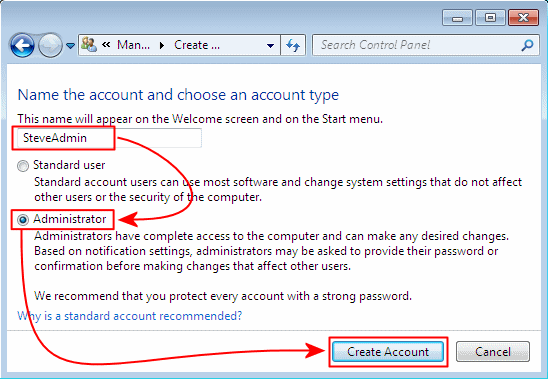 Create a new SteveAdmin user
Create a new SteveAdmin user
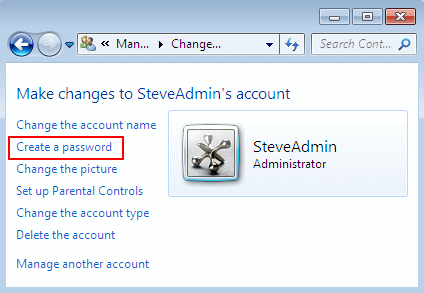 Assign a password to the new user SteveAdmin (if desired)
Assign a password to the new user SteveAdmin (if desired)If you do this, SteveAdmin will lose all EFS-encrypted files, personal certificates and stored password for Web sites or network resources.
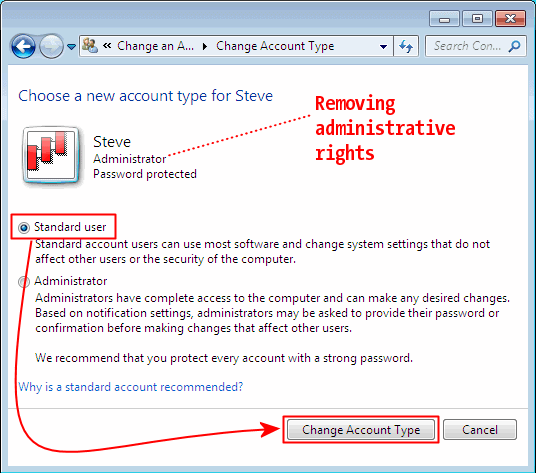 Demote the user "Steve"
Demote the user "Steve" Once logged in as a limited user, attempts to perform admin tasks are greeted with a UAC prompt asking for credentials for the SteveAdmin user.
At this point, one of the two procedures has set up a limited user Steve and a proper administrative account SteveAdmin, but some users might have previously enabled the built-in Administrator account as well.
I believe this is a bad idea, and recommend that the account be disabled. This won't be required if you've just installed Windows 7 freshly, or if Administrator does not appear on the login page as an icon for a user who can login.
If you're not sure, the steps to check and disable are almost the same:
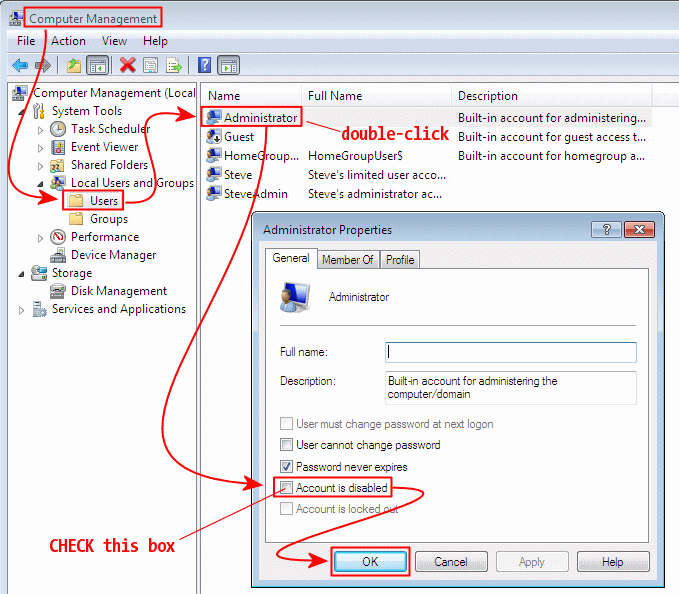 Open the "Manage Users" applet
Open the "Manage Users" applet
At this point, the Administrator account is disabled and cannot be
used to login or to approve UAC elevations. It's not necessary
to change the account's password, as disabling the account overrides any password
(even a blank one).
![]() Curiously enough, it's not always necessary to have a password on an account.
Since an account with a blank password cannot be accessed over the network,
you can substantially reduce the attack surface of a machine this way.
Curiously enough, it's not always necessary to have a password on an account.
Since an account with a blank password cannot be accessed over the network,
you can substantially reduce the attack surface of a machine this way.
But this requires that you have good control of physical security over the machine: if there are users on the machine (or in the environment) who are not allowed to perform administrative duties, it would be a poor idea to have a blank password because it would allow anybody to walk up to the computer and go to town.
In addition, a laptop that leaves the house is probably not a good candidate for a blank password because physical security is seriously problematic.
For most home users, it probably doesn't really matter that much how you choose your password schemes, but if you have any questions about this, please present your scenario to a trusted security adviser for guidance.
As noted before, I'd not set up Vista before, so were unaware that the Administrator account was disabled by default. This lead to an uncomfortable surprise after demoting the installation account Steve.
After configuring our machine, I'd gone into the Control Panel to downgrade the Steve account to a Standard User. I had unknowingly removed the only remaining admin account, so after logging out and back in (to allow the account change to take effect in our session), the next UAC operation provided this prompt:
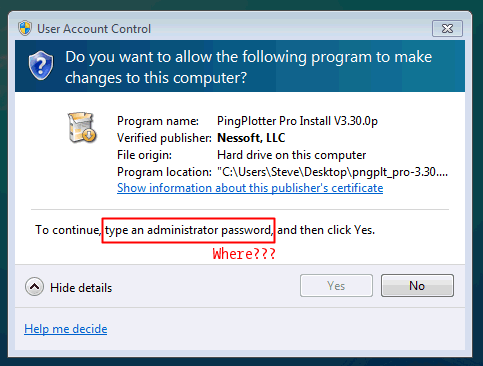
The careful reader will note there is no place to enter a password!, and to say that was maddening would be an understatement. Depending on your computer's configuration, there may be an invitation to use a Smart Card, but that won't likely do much good on a computer that's not had smartcards configured.
It seems like a poor user experience even though technically it was my own fault.
Special thanks to fellow MVP Susan Bradley and Microsoft smart guy Crispin Cowan, PhD for their invaluable assistance with this paper.
First published: 2009/05/27 (blogged)